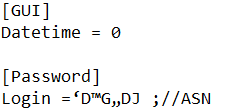- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LabVIEW string encryption
Solved!10-30-2020 09:01 AM - edited 10-30-2020 09:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
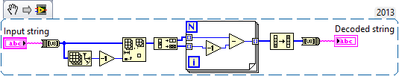
Hello everyone, I am kind of new to LabVIEW and I have been assigned to update an old project in which there is a VI for decoding encrypted string however the encryption VI seems to be missing.
I have attampted to guess the encyption algorithm based on the decryption VI below but nothing worked for me yet.
I am starting to run out of ideas, any help on this meter is much appreciated.
Regards.
Solved! Go to Solution.
10-30-2020 09:24 AM - edited 10-30-2020 09:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
Hi kuroro,
@kuroro_W wrote:
I have attampted to guess the encyption algorithm based on the decryption VI below but nothing worked for me yet.
What have you attempted?
Can you upload your VI?
Can you provide example data of encrypted strings with known "decoded" results?
This VI does:
- Delete the last byte.
- Decimate into 2 byte streams.
- For each pair of bytes: Decrement the 2nd byte and subtract the decremented value from 1st byte.
- Reverse the resulting byte array.
So the encryption should:
- Reverse the string/byte array.
- For each byte b0 in this array find two bytes b1/b2 where b0=b1-b2+1.
- Interleave the b1/b2 byte arrays.
- Add one more byte to get the encrypted string.
A simple implementation might look like this:

I simply set b2=1 to fulfill the decoding condition…
10-30-2020 09:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
Hi!
If You are new to LabVIEW, You might want to check out some online learning resources to get started. If You hover over a function and activate the context help (Ctrl+H), You can read a short description of the function and get a link to a more detailed help page.
What have You tried? Were You able to identify all parts of the code?
Apart from that: Are You sure that this is part of production code and not a homework assignment? If so, the first thing I suggest would be to crename "Decoded" to "Deobfuscated". Calling it Encryption and Decryption would be dangerous, as someone might be tempted to actually rely on the security of this algorithm.
10-30-2020 10:53 AM - edited 10-30-2020 10:58 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
Consider starting over... I don't know who came up with your encryption algorithm but it seems to be security by obscurity, and that's not a good idea.
Basic encryption is quite simple and very secure.
Encrypt: XOR the data with a repeating "encryption key". (a string of ASCII characters)
Decrypt: XOR the data with the encryption key.
The longer the key the stronger the encryption. ("128bit encryption" is a 128 character encryption key) Try to guess that 😛
=== Engineer Ambiguously ===
========================
10-30-2020 10:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
@GerdW wrote :
So the encryption should:
- Reverse the string/byte array.
- For each byte b0 in this array find two bytes b1/b2 where b0=b1-b2+1.
- Interleave the b1/b2 byte arrays.
- Add one more byte to get the encrypted string.
That is exactly what I thought and I am stuck in step 2. I have been trying to find the relation between b0, b1 and b2 using a decoded word I found in a ini file with the project which gives this in the decoding VI.
For step 4, I am guessing the last byte could be a kind of checksum but I will worry about that later 😅
10-30-2020 11:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
@RTSLVU wrote :
Consider starting over... I don't know who came up with your encryption algorithm but it seems to be security by obscurity, and that's not a good idea.
It would be easier to start over and there is many examples online. Howerer, this is a running project and this meant to be a simple upgrade and should not affect the existing products 😣.
11-01-2020 04:56 AM - edited 11-01-2020 05:02 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
Basically if the function you showed is the only consumer of that obfuscated.string, the function Gerd showed would be all that is needed. To make it look actually obfuscated you could replace his 1 constant with a random number unsigned 8-bit integer between 0 and 255, and decrement and then add that from the real character code. Since the actual “encryption key” is fully embedded in the “encrypted result” it doesn’t matter what “encryption key” you use, as proven by Gerds code that uses a constant “encryption key”.
To make it even more complicated but not a yota more secure you can calculate a new random number for each individual character.