- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Double XOR Cipher Will it increase safety?
10-20-2021 09:30 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
I have just come into contact with the XOR Cipher encryption method, and I heard that as long as the frequency analysis is used, this simple mutual exclusion or cipher can be cracked.
So if I encrypt the text that was encrypted the first time with the second set of passwords, will this increase the difficulty of cracking?
I am not very proficient in mathematics. But thank you very much for your replies, this will let me learn~
10-20-2021 09:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
10-20-2021 10:01 AM - edited 10-20-2021 10:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
@koukileo wrote:
I have just come into contact with the XOR Cipher encryption method, and I heard that as long as the frequency analysis is used, this simple mutual exclusion or cipher can be cracked.
So if I encrypt the text that was encrypted the first time with the second set of passwords, will this increase the difficulty of cracking?
I am not very proficient in mathematics. But thank you very much for your replies, this will let me learn~
Yes, no, maybe...
There's really no mathematics going on besides Boolean Logic in a simple XOR encryption.
The question is how secure do you really need to be?
Here's a page that links to a couple 3rd party encryption add-ons
Here's an open source AES library for LabVIEW
Consider taking a close look at the Open Source AES library source code to learn how they implemented AES.
=== Engineer Ambiguously ===
========================
10-20-2021 10:08 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
@koukileo wrote:
So if I encrypt the text that was encrypted the first time with the second set of passwords, will this increase the difficulty of cracking?
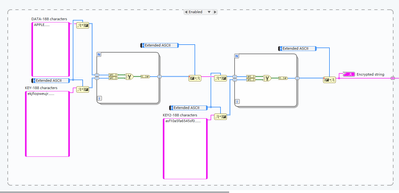
Not enough to matter. But this the basic idea behind Triple DES (encrypt with key A, decrypt with key B, encrypt with key C). But DES already has a much higher security rating, so this actually does increase security significantly.
2 comments on your code:
1. NXG is now obsolete. You should consider switching to LabVIEW 2020 or 2021.
2. The XOR node can accept integers, even arrays of integers. So there is no need for the converting to/from boolean and even the FOR loops.
There are only two ways to tell somebody thanks: Kudos and Marked Solutions
Unofficial Forum Rules and Guidelines
"Not that we are sufficient in ourselves to claim anything as coming from us, but our sufficiency is from God" - 2 Corinthians 3:5
10-20-2021 10:12 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
Since XOR is associative and commutative it doesn't help.
Applying the XOR twice with different "passwords" is exactly the same as applying once, except the password used is (Password1 XOR Password2).
It is this combined password that would be revealed just as easily as a single password using the same analysis technique.
0xDEAD
10-20-2021 11:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
Not saying anything new, but here's how I'd approach it:
1. Am I mostly concerned with how secure the end result is? Then I'd use one of the many free encryption tools available that will give much better security.
2. Am I mostly just a little curious about what encryption means and how I could implement it in code? Then some simple, reversible techniques like XOR or ROT13 are a fine place to get started.
-Kevin P
10-20-2021 11:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report to a Moderator
What does encryption have to do with "safety"?