From Friday, April 19th (11:00 PM CDT) through Saturday, April 20th (2:00 PM CDT), 2024, ni.com will undergo system upgrades that may result in temporary service interruption.
We appreciate your patience as we improve our online experience.
From Friday, April 19th (11:00 PM CDT) through Saturday, April 20th (2:00 PM CDT), 2024, ni.com will undergo system upgrades that may result in temporary service interruption.
We appreciate your patience as we improve our online experience.
*Please add your country to the title of your project, example: Amazing Robot Project, Poland.
University:National Institute of Science and Technology
Team Member(s):Stita Pragyan Dandapat and Ashirbad Das
Faculty Advisors:Mr. Kunja Bihari Swain
Email Address:stita123@gmail.com
Country:INDIA
The aim of this project is to hide or embed a data image on a cover Image at the encoding level and extract this data image from the cover image at the decoding level to enhance the cyber security
1) NI Labview 2011
2) NI Vision Acquisition Software 2011
3) NI Vision Development Module 2011
4) Any USB camera/other image capturing devices
Steganography is the art of hiding the fact that communication is taking place, by hiding information in other information. Many different carrier file formats can be used, but digital images are the most popular because of their frequency on the Internet. For hiding secret information in images, there exists a large variety of steganographic techniques some are more complex than others and all of them have respective strong and weak points. Different applications have different requirements of the steganography technique used. For example, some applications may require absolute invisibility of the secret information, while others require a larger secret message to be hidden. In this project a data image is to be hidden inside a cover Image at the sender's point and at the receiver's point that data image is to be extracted from the same cover image.
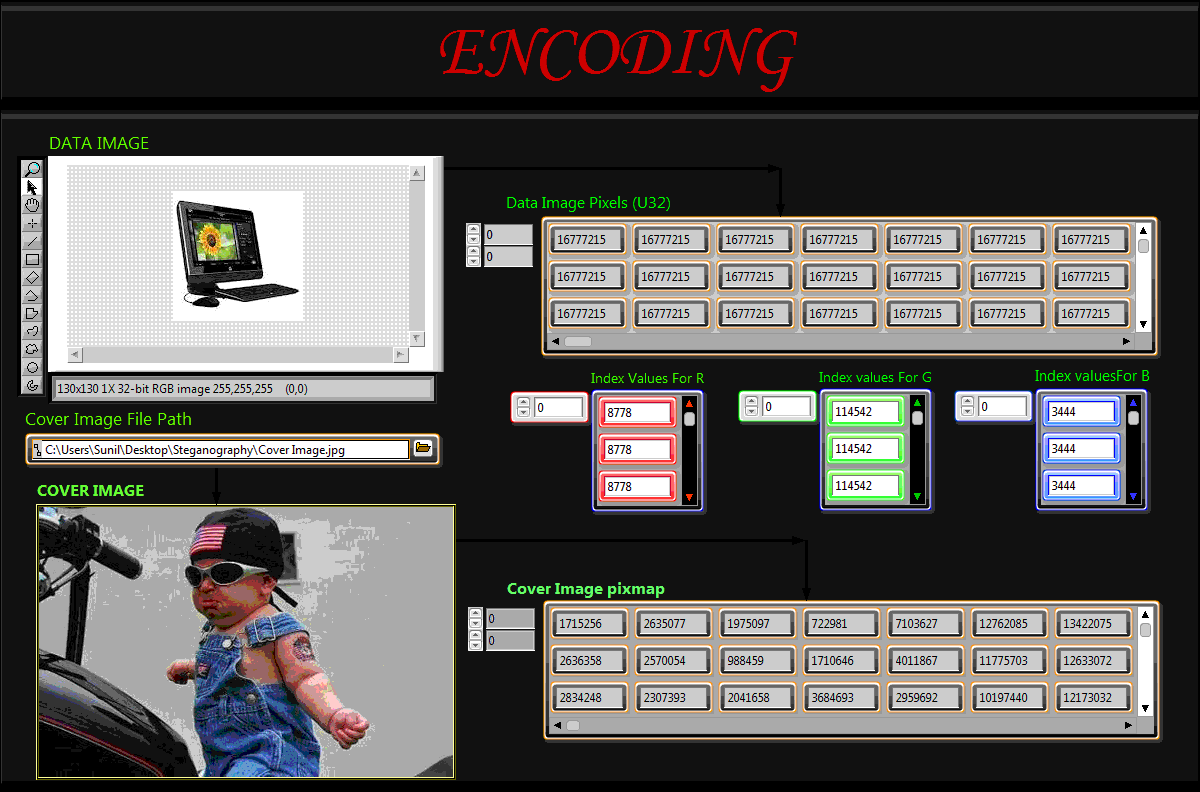
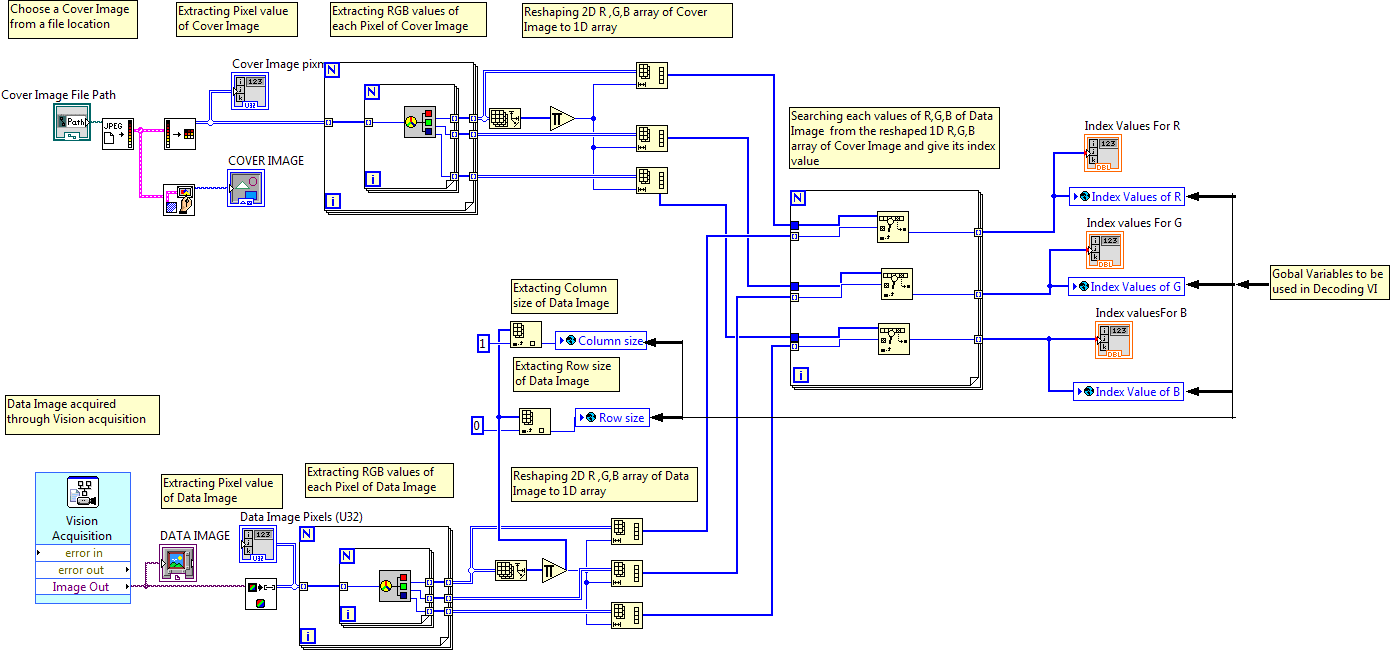
At the Encoding part first a data image is captured through a vision acquisition device(for experiment we took a usb camera) and the cover image is given through a file location, then the data image and cover image R,G and B values are extracted. After extraction of the R, G and B values of the cover image and data image,each R, G and B values of the data image is searched with the R, G and B values of the cover image and their index values are stored in an array and passed to Gobal variables that is to be used in Decoding part of our program along with the row and colum size of the data image.
NOTE:- As we are passing only the index arrays and the row and column size of the data image so it will be very difficult to a third party to get any imformation about our data image and it will be secured.
FRONT PANEL:-
BLOCK DIAGRAM:-
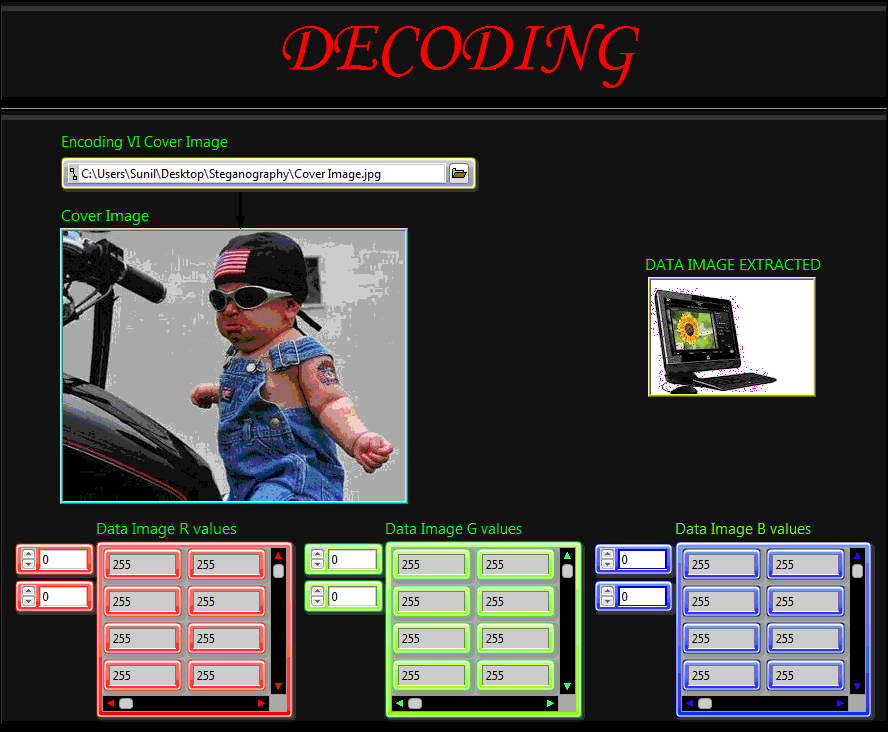
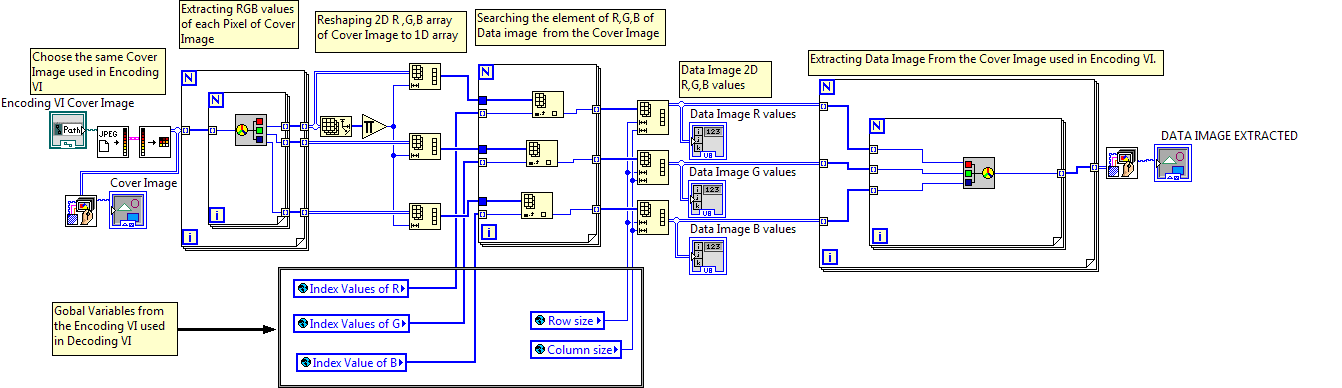
At the Decoding part the cover image used is provided and its R,G and B values are extracted and then using the index array function the elements at each index present in the index arrays of R,G and B(got from the Encoding part of our program) are extracted and finally combined to get the Data Image.
FRONT PANEL:-
BLOCK DIAGRAM:-
GLOBAL VI USED IN BOTH ENCODING AND DECODING PART OF THE PROGRAM:-
APPLICATION:-
Image Steganography has many applications, especially in today’s modern, hightech world. Privacy and anonymity is a concern for most people on the internet.
Image Steganography allows for two parties to communicate secretly and covertly. It allows for some morally-conscious people to safely whistle blow on internal actions;
it allows for copyright protection on digital files using the message as a digital watermark. One of the other main uses for Image Steganography is for the transportation of high-level or top-secret documents between international governments.
USES:-
This technique can be used in satellites to transfer highly confidential image data to their workstation,can be used at military bases etc where data security is very much essential.
Nominate Your Professor: (optional)
<insert nomination. Does your professor use LabVIEW or other National Instruments technology to make learning difficult concepts engaging, interesting, and fun? If so, nominate him/her as an outstanding educator by telling us who they are, what they teach, and how they make learning a better experience for you.>
a good idea being implemented in this project....which is very much necessary now a days.......do lyk it....
good project
thanks.............
good 1..........
Thank U subham.....................
Nice work
Gud Project !!!!!!!
first extract the data in the form of matrix, by assigning color intensity or values for green, red and blue, find orthogonal(PCA) arrays parsing maximum number of data points possible. Capture any two the arrays with maximum variance, plot graph betwn those two arrays u ll get clusters, model the clusters using statistical Neural network modelling use the model in place of image. hehehehhehe very easy
kk next time i will try ..............................n thanks..........
Good idea being implemented....................
very nice project.... great work......Ashirbad and Stita.....
nice project. keep it up
Thank you amlan...........
Thank u Roshan
superb dear.............keep it up
Oowoooooo ......quite interesting .......!!!!!!!!!! anyws superbly done...... ![]() kp it up ......!!!!!!!
kp it up ......!!!!!!!
good....keep it up.....![]()
Keep up the good work.The project looks great ,and may you carry on with your journey 🙂
gud 1
G-One
Nicw work!! Best of luck!!
good one and i learn how to use global variable. ![]()
Great and simple ... Effective coding.
i am using labview version 10 so i cant open global variable.vi can anyone please save it as compactable for version 10 and please send me my email id is ansu.francis3@gmail.com
is any one tell me what is latest technology or algorithm is used for image steganography?
how did you create the global variables ?