Cryptography
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report to a Moderator
Code and Documents
Attachment
Crypto-Tools for LabVIEW contains Crypto.llb and Large Numbers.llb, follow ciphers are available:
DES, 3DES, AES, IDEA, Blowfish, RC4, 3PP, RSA, ECC (elliptic curve cryptography), DSA, RSADSA, ECDSA, MD5, SHA-1, SHA-2, HMAC, PBKDF2, Enigma and Steganography, the vi's uses only standard LabVIEW functions.
Alfred Lauper, 21.03.2015
http://www.wingover.ch/Kryptographie/

Additional dotNET CryptoService.llb uses the Crypto functions from dotNET.
Example code from the Example Code Exchange in the NI Community is licensed with the MIT license.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
A great collection of tools for cryptography. I just need it recently. Thanks, Wingover. ![]()
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello Wingover, can you give me an idea how much information can be stored in a given picture for steganography?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello, you can use 3 bits of the 8 bit colour for data encryption (37% of the uncompressed picture).
With a 270x360 pixel picture it is 3bit*270*360*3 /8 = 110kByte.
Best regards, Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hi all, I am new to the labview and i wonder if I could find any tutorial for using this tool and how possible to connect it with Arduino mega 2560. By the way i have already installed the library as well as arduino in my labview. Arduino is working fine but, I need some tutorial on how to connect the cryptography with it.
BR//
Mohammed
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello Mohamed,
Crypto-Tool is a privat work without a manual. But you can see how cryptography in LabVIEW works.
There is no connection to your uP-Board. I think it's better you look for cryptography-modules in C-language.
Best Regards, Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Great collection of crypto tools. I have learned a lot going through it!
Question:
When running the RSA example with a "large" key size, it overloads the fastest PC I have (Quad core Xenon). The example has a default keysize of 50 bits but I read that secure RSA requires at least 1,000 bit keys (or larger). Setting the size to 1,000 takes 10-15 minutes to compute the primes. If I bump it to 2,000 it bogs down and I have not been able to run it long enough to find primes. I have left it running for hours and still does not find primes.
Maybe I am misunderstanding the definition of key length? Is it p+q = 1,000 bits or is it the sum of all keys, public + private?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
The key length = lng(p) + lng(q)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Is still toolkit free of license / use for a commercial project ?
Senior Project Engineer / CLA
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Be careful using this for commercial purposes even if the license is free. The code is well written and appears correct but I am no crypto expert. Offering an unproven crypto solution to a customer is a risky thing. There are tested dll files and/or dot-net assemblies out there that you could call with good confidence.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
this tool is license free but it is your responsibility what you do with it
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
wingover,
Question about LN - Primzahl.vi
In this VI, a large random number is generated and then some other numbers are chosen to be added to this number. Then these numbers are sent to Rabin-Miller for primeality testing.
The code starts with division by small primes (which makes sense) but then it goes way beyond that. I can see what the code is doing but I can't figure out why this is being done. What is this algorithm based on?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello,
the number of possible primes is first reduced with the sieve of
eratosthenes algorithm
Example: start with 100
Range: 100 .. 110
100/2: delete 100 102 104 106 108 110
100/3: delete 99 102 105 108
100/5: delete 100 105 110
Rest: 101 103 107 109 => Miller-Rabin check
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
I took a closer look at Primzahl.vi and here is what it is doing:
n = initial random large number seed
z = 0.1*log2(n)^2 (approximately)
Create Array A[] = sequential integers from 0 to z-1
p[] = array of small primes generated by "LN - Small Pirmes.vi" (contains the first z primes)
For i=0 to i >= z
k = n mod p
While j*P-k > z
mark A[j*P-k] = -1
++j
++i
Now loop through A[]
Take all values != -1 and add them to n to build array P[]
Send P[] to miller-rabin test
Why this works is mysterious to me. Basically it takes a large random prime candidate and adds seemingly random numbers to it to generate an array of prime candidates that are relatively near each other. This seems to be as good as if not better than generating a group of random candidates and using eratosthenes to eliminate numbers with small factors.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Further tweaks: Create random numbers between zero and (0.1*log2(n)^2). These numbers are added to the initial candidate "seed". Then, numbers sent to miller-rabin have LSB forced to = 1. This cuts the time to find primes in half for obvious reasons!
Still very slow so mostly for educational purposes. On my quad core Xenon, takes about 15 min to find 1000 bit primes. 8-10 hours to find a 3,000 bit prime!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Thanks for your comment. The prime number calculation is really very slow.
If the Prime is searched over random numbers, the calculation process takes
three times longer.
Maybe you got the wrong control input at the is not connected, the default value of 32 bits is used.
Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
I have tried several large number generation methods and the ratio of primes seems to be the same. Roughly 70% of random or semi-random numbers will be composite with one of the first 10 primes, 80% if checked agenst the first 100 primes. Not much to be gained by checking more than the first 100 primes before sending to Miller-Rabin.
There must be some much more efficient way of searching primes because I can ask the dot net crypto library to generate a 3000 bit RSA key and it only takes a few seconds. Not that Microsoft will share what it is...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
The base of functions are probably too slow. The most time is
claimed by the div function.
If the selected random number can be divided by two, it is clear that this
can not be a prime number. This fast test can repeated with the next primes
3 5 7.... This increases the probability that it is a prime number. The
sieve of eratosthenes is the best way to do that. Such solutions you get, if
you try to accelerate the prime number seek.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Mostly this proves that LabVIEW is not the right tool for this task. Maybe if you used NI FPGA?
I expect that the code running on high volume HTTPS servers is written in assembly and can find hundreds of 3kbit primes per second.
Or they have switched to ECC and are using 300-400bit primes.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello,Wingover
I want RC4 tool for my application. That means i need crypto.llb.
Can i get this Crypto-tools for lower ver of LabVIEW. i.e for LabVIEW 2011.
if it is possible to get this tools, mail me or suggest me the source to get it.
Mail ID :- mihir.mahajan@sprylogic.com
Thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello!
Like mihir8181, I need crypto.llb for LabVIEW 2011.
I hope that you can help me. Let me know if it is possible to have it.
Thank you!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
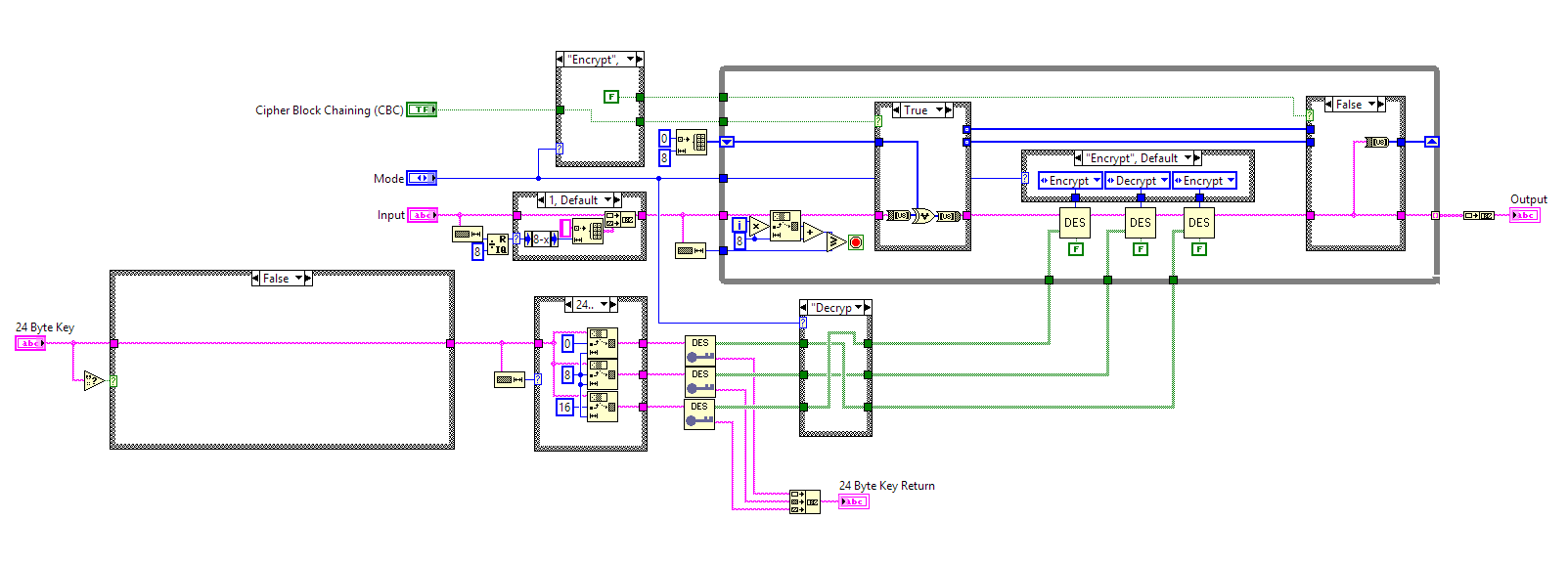
Hi,
i have many keys that were built using 24 byte key on Tripe DES.
your VIs seems to limit to 14 byte. is there a way this can be used with 24 Byte keys (option 1, K1)
how do i need to modify in order to decrypt my text using 24 byte keys.
Please help
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Problem is that there are a number of different 3DES versions out there and the author of this code implemented only one version.
Best I can tell from reading about the Triple DES algorithm, you would need to modify the code to take your 24 byte key, and split it into three 8 byte chunks. Then run these 3 chunks through the DES Keygenerator.vi and feed the resulting three subkey arrays into the DES rounds so you would have 3 unique subkeys instead of 2 like in the original code. Beyond that, it will depend on which exact version was used for your 24 byte key version. You may need to try some tweaks to get exactly the same mechanism as your original encryption used.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
@ freemason
the 3Key 3DES uses 3 x 8 Bytes Key and is the same DES algorithm
by Decoding the keyorder has to be changed
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
@wingover
3DES Questions:
1) If CBC is False, what's the mode of operation? is it ECB?
2) If CBC is True, what is the IV (initialization vector) value?
How did you validate that the implementation is working correctly? I tried playing around but I got different results using different 3des online tools.
Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
@ejohn73
1) if CBC is False, 3DES mode is ECB
2) if CBC is True, 8Bytes IV is 0
BR
Alfred Lauper
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
How did you validate the results? What tool/s did you use? I'm using this online tool (http://tripledes.online-domain-tools.com) for validation but the results did not match.
Thanks for the help!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
try this
http://www.scs.stanford.edu/histar/src/pkg/uclibc/test/crypt/crypt.input
there are different modes and padding methods
BR
Alfred Lauper
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
I'm using a tool named "ctbrowse" from Safenet. Here are the parameters of my test:
1) Mechanism: 3DES_ECB
2) Input text: test123
3) Cipher test (HEX): 59E328DCA6B71E2E
4) Key (HEX): 9179B06E 7C25AB1C 16EFA4F2 64C7E507 B9613267 0480CE15
Could you possibly verify this using your 3DES vi?
Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
It is a 3TDES algorithm with 0x00 padding
BR, Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
It is a 3TDES algorithm with 0x00 padding
BR, Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Is there a way "not to use" the 0x00 padding?
Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
you can use any char for padding. But the encryption result is different
http://www.di-mgt.com.au/cryptopad.html
1. Pad with bytes all of the same value as the number of padding bytes
2. Pad with 0x80 followed by zero bytes
3. Pad with zeroes except make the last byte equal to the number of
padding bytes
4. Pad with zero (null) characters
5. Pad with space characters
3TDES Algorithm.vi
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Got this example from the link you give:
Example using Triple DES with key 0x0123456789ABCDEFFEDCBA987654321089ABCDEF01234567
ASCII PLAINTEXT: 123453760666666555551205
3DES INPUT BLOCKS: 12345376 06666665 55551205
INPUT IN HEX: 3132333435333736 3036363636363635 3535353531323035
3DES OUTPUT: 7ADE45981580DB32 421E3D90B5B47D5B 1175FA3DD8B932D7
I use the 3TDES Algorithm.vi (ECB) with the 16-byte Key 0123456789ABCDEFFEDCBA9876543210
3DES OUTPUT: 57CE 519D 480E 74C9 7C4D 2ABC BFB4 F207 DF7F 0366 5E39 BD1C
3TDES Algorithm.vi OUTPUT: 30E5 8052 46AA F733 B254 F457 C5B3 1E25 44AF 9DDD 7FB6 F66A
Is the input still padded?
Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello,
First of all, thanks for this wonderfull library!
I am using the RSA algorithm to sing the SHA256 hash.
I am new in this security world, and I don't understand how to pass the public key and private key (I am using .pem files)
to exponent and modulo keys.
How I can use the library to sing the SHA256 with the private key (and how to use the 1024bit .pem key to do it?)
I am going in a good way?
Thanks a lot!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello
the output of 3DES is 0x30E5 8052 46AA F733 B254 F457 C5B3 1E25 44AF 9DDD
7FB6 F66A
and 3DES ist padded with 0x20
the 3TDES is padded with 0x00 as your example
BR, Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Unfortunately I can not help you.
I do not know the pem file format
Did you try the RSA-DSA.vi?
BR, Alfred
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello Alfred,
I am trying to use the PBKDF2 VI that you have uploaded but when I tested its output against some standard test vectors I kept getting a different result. I managed to get some help with testing the original Java script implementation and its output matched the test vector result. I have tried to research and find what the problem might be, but I am relatively new to LabVIEW, Cryptography and Java, and I can’t see any clear issues. Is there any change you can review the PBKDF2 VI? as you may know where the problem is occurring.
Kind Regards,
Shabaj
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Hello,
I just found the problem with the PBKDF2 VI, the salt does not need padding. To fix it I removed the case structure and wired the string directly into the for loop. Now the output matches the test vectors.
Regards,
Shabaj
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
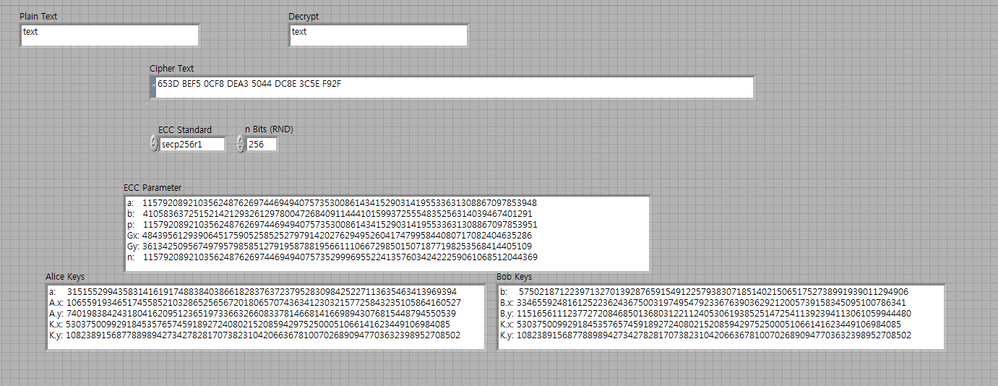
Hey I am trying to use the ECC function in secp384r1 standard. I am expecting the keys to be 48 bytes length but I am getting 58 bytes. No clue what to change.Can you please help me.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
I want to create private and public keys using ECC.
So I used the llb I uploaded, but I do not know which is the private key or the public key.
How can I check?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Are there authenticated encryption algorithms (eg GCM) available? I'm mostly just looking to dodge padding oracle attacks that one might encounter if they were to "roll their own".
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report to a Moderator
Is there any labview code for the key generation used in WPA3 protocol. for example Diffie-Hellman key generation code. ?